Difference between revisions of "Goggle"
| (6 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
[[File:goggle.png|center|500px]] | [[File:goggle.png|center|500px]] | ||
'''Goggle''' was a '''''typosquating''''' domain that was registered in 1998. Around 2004, '''Goggle''' became a site that preyed on Windows 95 users who were still using that operating system because they were too cheap to upgrade to Windows Vista. These days, '''Goggle''' has been pretty much removed from the internet. Mostly because Google doesn't have a fucking sense of humor. | '''Goggle''' was a '''''typosquating'''''<ref>https://www.macmillandictionary.com/us/dictionary/american/typosquatting</ref> domain that was registered in 1998. Around 2004, '''Goggle''' became a site that preyed on Windows 95 users who were still using that operating system because they were too cheap to upgrade to Windows Vista. These days, '''Goggle''' has been pretty much removed from the internet. Mostly because Google doesn't have a fucking sense of humor. | ||
==Typosquating?== | ==Typosquating?== | ||
[[File:goggletypo.jpg|right|170px]] | |||
Typosquatting is a type of social engineering attack which targets internet users who incorrectly type a URL into their web browser rather than using a search engine. Typically, it involves tricking users into visiting malicious websites with URLs that are common misspellings of legitimate websites. | Typosquatting is a type of social engineering attack which targets internet users who incorrectly type a URL into their web browser rather than using a search engine. Typically, it involves tricking users into visiting malicious websites with URLs that are common misspellings of legitimate websites. | ||
| Line 14: | Line 14: | ||
==The Windows Metafile Exploit== | ==The Windows Metafile Exploit== | ||
[[File:wmf.jpeg|right|200px]] | |||
First off, the microsoft guys who thought up the Windows metafile format were idiots. Secondly, I am sure they thought nobody would ever think to do what malicious coders might do... | First off, the microsoft guys who thought up the Windows metafile format were idiots. Secondly, I am sure they thought nobody would ever think to do what malicious coders might do... | ||
| Line 21: | Line 21: | ||
We aren't talking about opening your CD tray to make it a cup holder anymore. This exploit was dangerous. | We aren't talking about opening your CD tray to make it a cup holder anymore. This exploit was dangerous. | ||
Basically, any person who clicked on an image, would begin a vicious cycle where the image would cause a ton of files to be downloaded in the background without the user's knowledge. | Basically, any person who clicked on an image, would begin a vicious cycle where the image would cause a ton of files to be downloaded in the background without the user's knowledge. | ||
==In Action== | ==In Action== | ||
| Line 42: | Line 42: | ||
==SpySheriff== | ==SpySheriff== | ||
[[File:gogglered.jpg|right|300px]] | |||
Remember all of those pop up advertisements you were furiously clicking to get rid of? Well '''Goggle''' had a ''coup de grace'' ready for your dumb ass if you were stupid enough to click on any of them. This final blow was SpySherif. | Remember all of those pop up advertisements you were furiously clicking to get rid of? Well '''Goggle''' had a ''coup de grace'' ready for your dumb ass if you were stupid enough to click on any of them. This final blow was SpySherif. | ||
| Line 65: | Line 65: | ||
==Windows Vista== | ==Windows Vista== | ||
As much as everybody | As much as everybody shits all over Vista, it actually patched the Windows Metafile Exploit. | ||
==McAfee== | ==McAfee== | ||
| Line 102: | Line 102: | ||
==References== | ==References== | ||
<references /> | <references /> | ||
[[Category:Internet]][[Category:IRL Shit]] | {{Websites}} | ||
{{Good}} | |||
[[Category:Internet]][[Category:IRL Shit]][[Category:Old]] | |||
Latest revision as of 02:46, 20 March 2023
Goggle was a typosquating[1] domain that was registered in 1998. Around 2004, Goggle became a site that preyed on Windows 95 users who were still using that operating system because they were too cheap to upgrade to Windows Vista. These days, Goggle has been pretty much removed from the internet. Mostly because Google doesn't have a fucking sense of humor.
Typosquating?
Typosquatting is a type of social engineering attack which targets internet users who incorrectly type a URL into their web browser rather than using a search engine. Typically, it involves tricking users into visiting malicious websites with URLs that are common misspellings of legitimate websites.
What Happened?
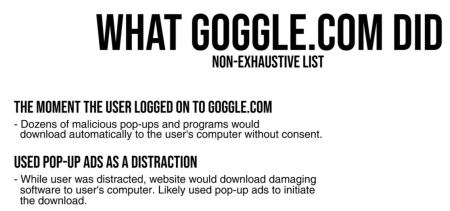
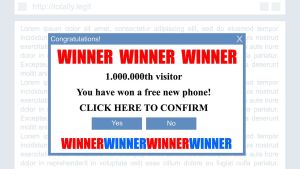
Back in 2004, you were probably too cheap to upgrade your OS and browser. Because you were so cheap, you were probably using something stupid like Windows 95 coupled with Internet Explorer. Then you decided to visit Goggle. when you meant to type Google into your address bar. Once this happened, you were treated with a bevy of malware, adware, trojans, scareware, ransomeware, and spyware. In layman's terms, you were shit outta luck.
Additionally, you got pop up ads that drove you insane. But that was just the start. While you were furiously clicking the X button to shut down the pop ups, because that is what everybody did back in those days, Goggle was using an exploit that was within the Windows operating system at the time.
The Windows Metafile Exploit
First off, the microsoft guys who thought up the Windows metafile format were idiots. Secondly, I am sure they thought nobody would ever think to do what malicious coders might do...
.WMF files were an image file that, when opened, executed a bunch of commands in the background. One of these commands was the gdi32.dll file that had the job of communicating with printers. It also had a huge vulnerability. This vulnerability allowed the .dll to execute ANY Windows command.
We aren't talking about opening your CD tray to make it a cup holder anymore. This exploit was dangerous.
Basically, any person who clicked on an image, would begin a vicious cycle where the image would cause a ton of files to be downloaded in the background without the user's knowledge.
In Action
Some examples...
Myspace
Researchers at iDefense this week identified a banner advertisement on MySpace.com that uses a Windows security vulnerability to download spyware onto an unpatched PC, another sign that cybercriminals quickly are catching on to the social networking site's massive popularity.[2]
Deckoutyourdeck
More than 1 million users of MySpace.com and other Web sites may have been infected with adware spread by a banner advertisement, according to iDefense, a computer security group. The advertisement, for a site called deckoutyourdeck.com, appeared in user profiles on MySpace, an online community with at least 70 million users, said Ken Dunham, director of the rapid response team at iDefense, which is owned by VeriSign Inc. The ad exploits a problem in the way Microsoft Corp.'s Internet Explorer browser handles Windows Metafile (WMF) image files.[3]
Washington Post
Unpatched Internet Explorer users who visited the websites that displayed the malicious banners would become infected by a Trojan horse. The Trojan would then download and install spyware that tracks the infected machine's web usage and displays pop-up ads. Thanks to the nature of the security flaw and the way Trojan horse's work, the malicious activity would go unnoticed by the user.[4]
SpySheriff
Remember all of those pop up advertisements you were furiously clicking to get rid of? Well Goggle had a coup de grace ready for your dumb ass if you were stupid enough to click on any of them. This final blow was SpySherif.
SpySheriff was a malware program that disguised itself as antivirus software. Once you got yourself out of the Goggle fog and thought that you were back onto the normal internet, SpySherif would start popping up a control panel that explained how many viruses, trojans, and other vulnerabilities you were now subjected to.
People retarded enough to go to Goggle were also moronic enough to give SpySheriff access to further Windows administrative permissions. SpySheriff would edit registry keys to the point where it was part of the Windows operating system. Once done, internet access was no longer possible unless you wished to only view the SpySheriff website.
SpySheriff also fucked with you by:
- Creating new administrator accounts
- Fuck with your system volume
- Do crazy shit with your preferences
- Change your wallpaper to something icky
- Turn off System Restore
- Crash your PC if you tried to uninstall it
- Eventually make your PC unusable
SpySheriff Today
These days, if you try to go to www.spysheriff.com[5] you will be met with webpages asking you if you are sure you want to visit the site, or a blank page.
Windows Vista
As much as everybody shits all over Vista, it actually patched the Windows Metafile Exploit.
McAfee
This was a McAfee Site Advisory commercial of what happens when you visited goggle.com (as of now, the site is dead. Try it: Goggle ).
Goggle Today
The internet has scrubbed Goggle entirely. It is nearly impossible to view archived versions of the site.
The Goggle.com domain has a reportedly checkered past,[6] with Malware Wiki[7] sharing that “Goggle.com was considered by some to be a dangerous typosquatting site for Google.com made in 1998 (but turned into [a] malicious site in 2004).” The Goggle.com domain is still on some blocklists because of this. Most broadband providers, Frontier, for example, blocks access to the page, warning of a potential scam.
According to Whois data, Google is now the registrant of Goggle.com after the domain moved from Uniregistry to Google’s MarkMonitor account this week. Goggle.com was previously registered to Goggle.com, Inc. Previous versions of Goggle.com have been excluded from Archive.org’s Wayback Machine. The search giant has also secured domain names Goggle.net and Goggle.org from Goggle.com, Inc.
Does Google Own It?
YES.
It’s unknown whether Google purchased the domain names, but the trio of Goggle.com, Goggle.net, and Goggle.org were part of the 2022 Right of the Dot auction.
With Goggle.com, Goggle.net, and Goggle.org under its ownership, Google has secured three key domains from a brand protection perspective. According to SimilarWeb,[8] Goggle.com received 466,800 visitors in July 2022, a significant number of people that were likely trying to get to Google.com.
2011 Loss
Google has lost its cybersquatting fight with typo-snaffle site goggle.com, enabling its owner to carry on enticing clumsy typists into signing up for pricey text messaging services.
The company's complaint against the domain name's current registrant, Barbados-based David Csumrik, was dismissed on procedural grounds yesterday by a three-person National Arbitration Forum panel in the US.
Right now, Goggle.com's website asks visitors a short series of questions before attempting to persuade them to sign up for a £3-per-text quiz competition, offering the latest Apple products as prizes.
2020 Election
For about six minutes, Goggle was a Wordpress site that tried to track the 2020 United States Presidential Election. As of 2023, Goggle is a 404.
References
- ↑ https://www.macmillandictionary.com/us/dictionary/american/typosquatting
- ↑ https://www.scmagazine.com/news/content/malicious-myspace-banner-downloads-spyware-in-latest-social-networking-attack
- ↑ https://www.helpnetsecurity.com/2006/07/20/protecting-myspace-users-against-ad-based-exploits/
- ↑ https://hothardware.com/news/spyware-infected-millions-via-hacked-ad-on-myspace
- ↑ Also known by numerous other names, including BraveSentry, Pest Trap, SpyTrooper, Adware Sheriff, SpywareNo, SpyLocked, SpywareQuake, SpyDawn, AntiVirGear, SpyDemolisher, System Security, SpywareStrike, SpyShredder, Alpha Cleaner, SpyMarshal, Adware Alert, Malware Stopper, Mr. Antispy, Spycrush, SpyAxe, MalwareAlarm, VirusBurst, VirusBursters, DIARemover, AntiVirus Gold, Antivirus Golden, SpyFalcon, and TheSpyBot/SpywareBot. The name SpywareBot is used to confuse them with the legitimate SpyBot anti-spyware software.
- ↑ DUH!
- ↑ The Malware Wiki is now gone... RIP
- ↑ https://www.similarweb.com/website/goggle.com/#ranking